Salesforce solutions and WordPress are two of the most widely used platforms globally, and that is certainly true for membership-based organizations. The ability to create a seamless, personalized experience across both platforms requires a type of integration commonly referred to as Single Sign-On (SSO).
For fusionSpan and our customers, this process can take one of several forms, but the basic tenets of each are rooted in two principles:
1) Expertise in the platforms involved (including Salesforce’s Fonteva platform and WordPress), and
2) Best practices for integration
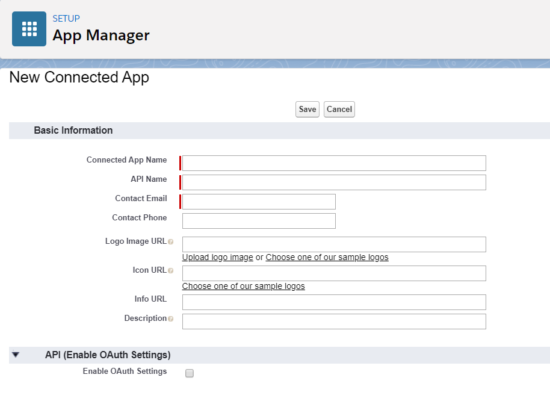
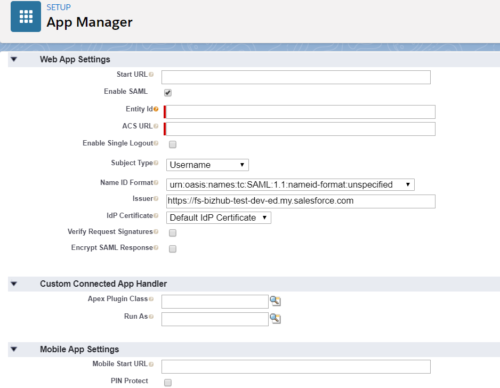
While there are “out of the box” plugins available for SSO, the complexity of some digital spaces and desired experiences sometimes require a specialized solution. The following highlights our method for a custom SSO solution that leverages standard capabilities.
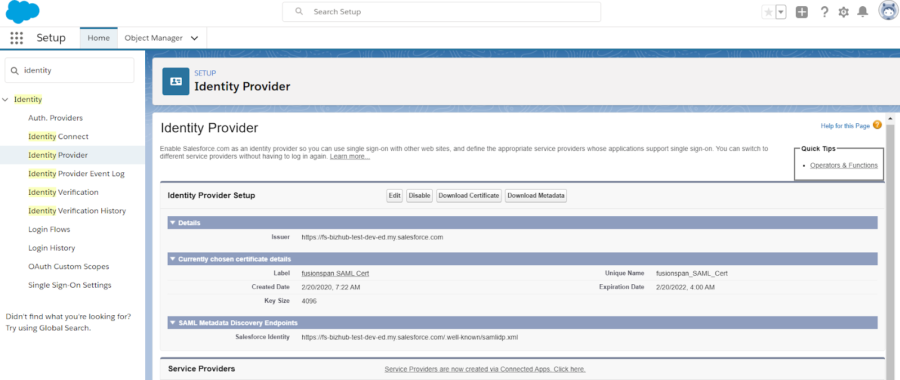
Single Sign On with Fonteva and WordPress for your Members
As we know, SSO is an authentication scheme that allows a user to log in with a single set of ID and password credentials to access any of several related, yet independent, software systems. As we have mentioned in previous blogs, SSO can take the form of a “Sign up with Google” or “Log in with Facebook” action button on your browser page.
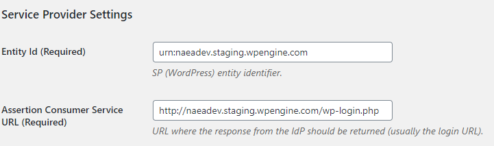
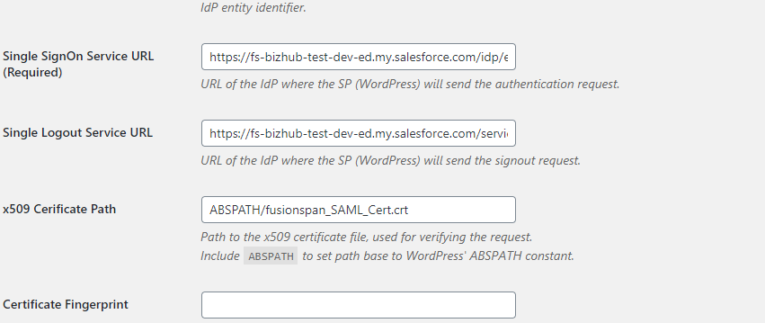
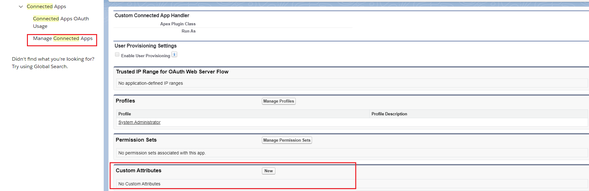
Security Assertion Markup Language (SAML) is the technique used which is an open standard for exchanging authentication and authorization data between parties. In particular, between an identity provider (a trusted provider that lets you use single sign-on to access other websites) and a service provider (in this case, one that needs the authentication from the identity provider to grant authorization to the user).